Principles
Cyber Tzar was established with the goal of improving the understanding and management of cyber risk globally to facilitate more fully informed interactions in the marketplace and promoting a safer and more secure internet.
The credibility of the score is key to its adoption and we have developed a number of principles to guide and communicate our approach.
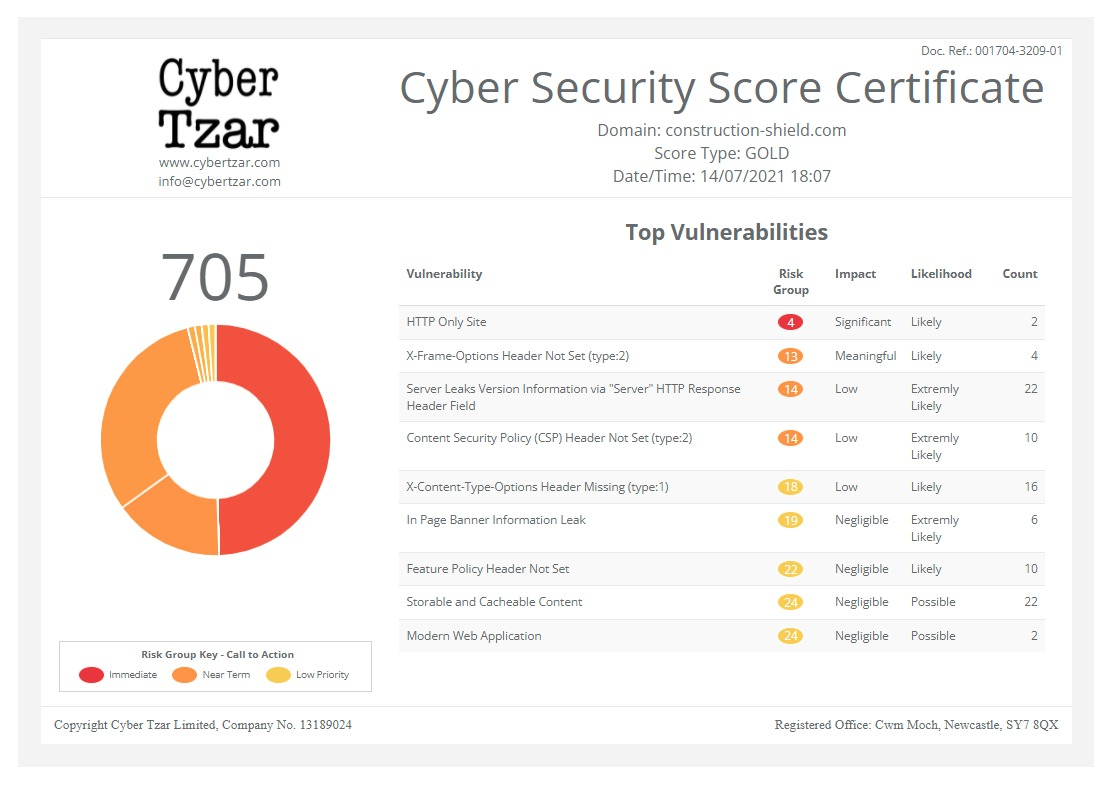
- Accuracy – Our most comprehensive Cyber Security Score is based on hundreds of thousands of individual tests together with a number of additional actions not undertaken by our competitors including, SSL Health Checks, Port Vulnerability Scans, and scanning of APIs.
- Fairness – Every client enjoys precisely the same level of scrutiny and a score based solely on the number and frequency of vulnerabilities discovered.
- Universality – The service is universally available allowing comparisons to be made between organisations anywhere in the world
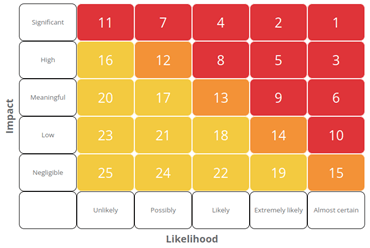
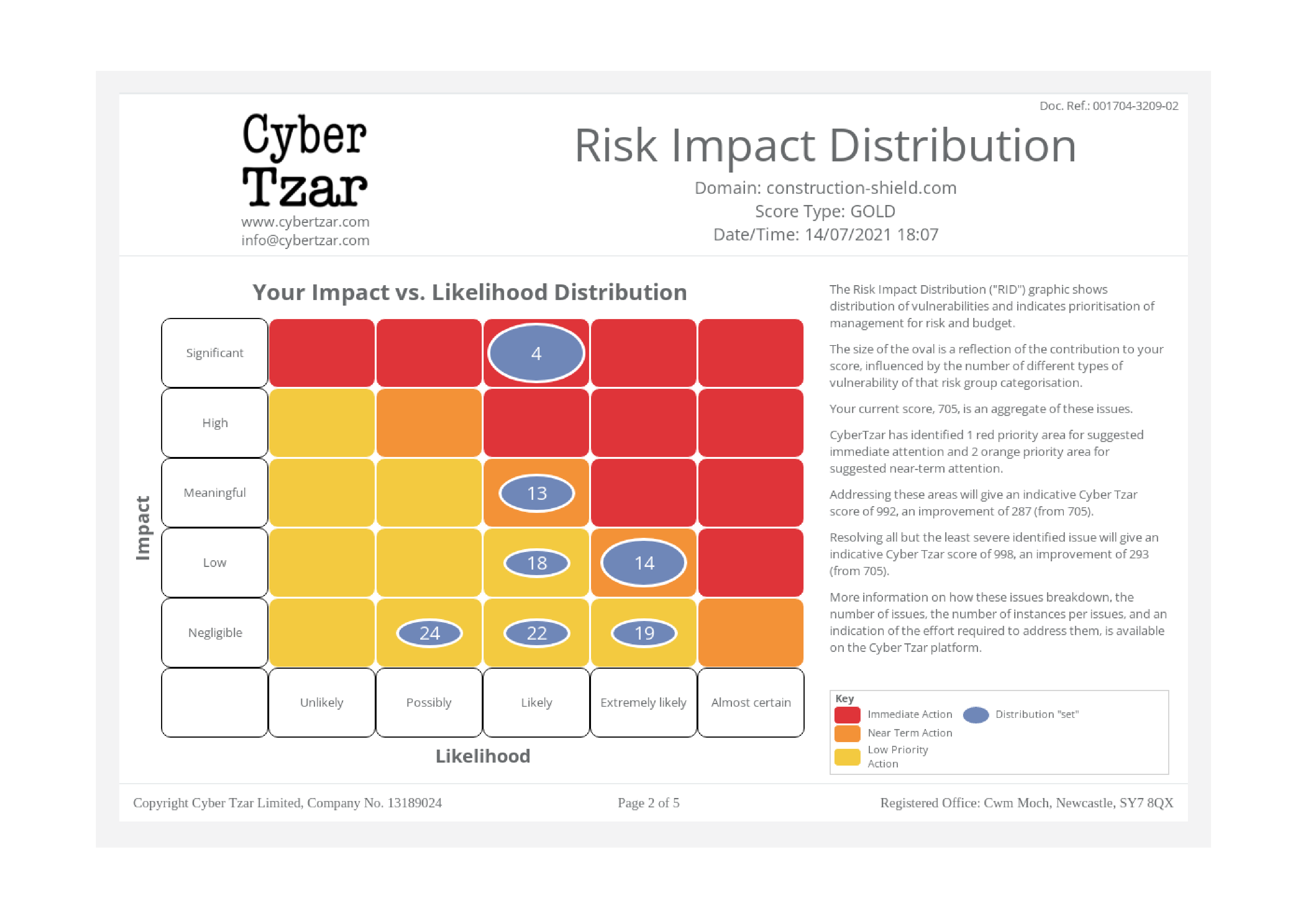
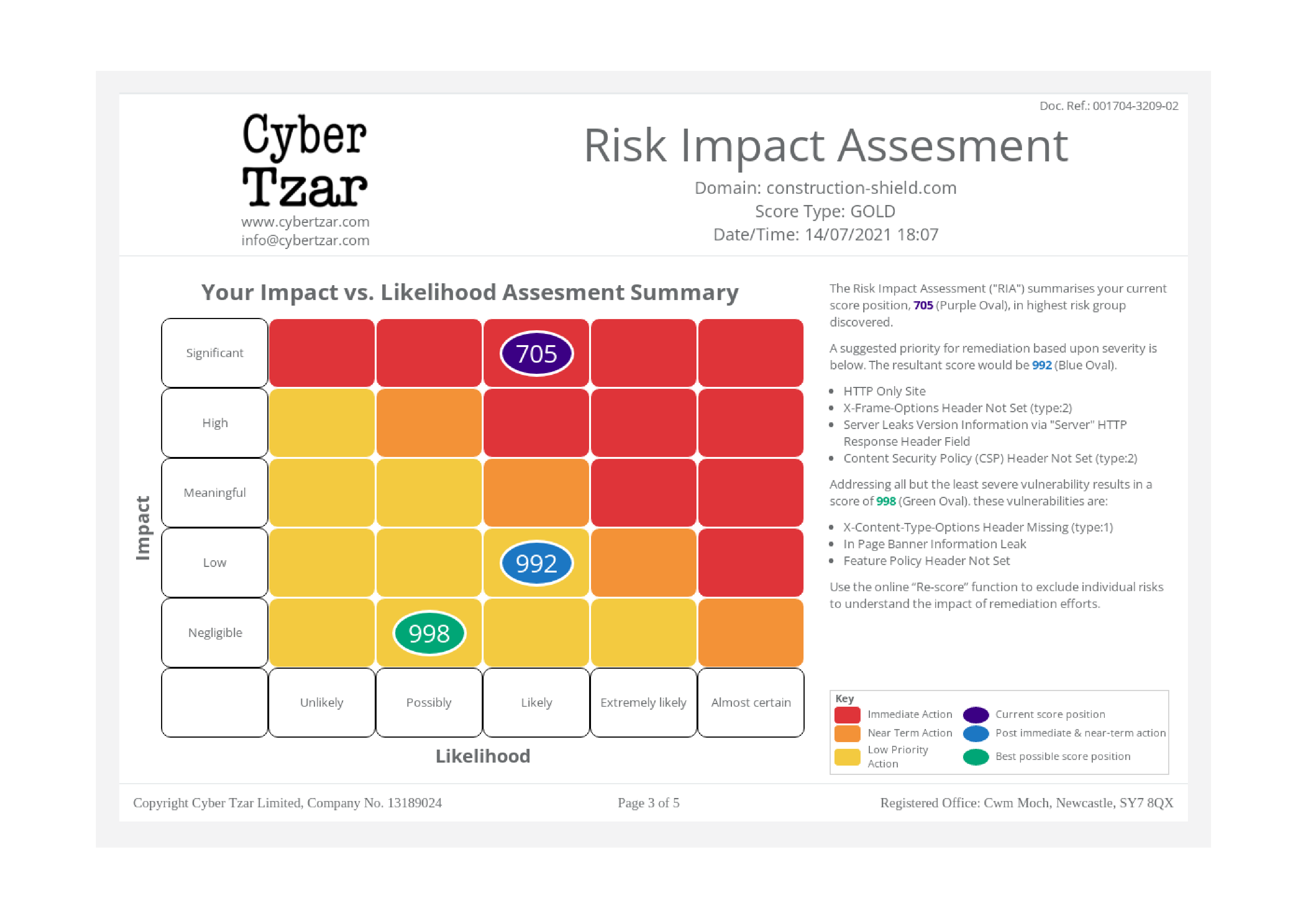
- Stability – The score is based on a quantitative analysis of vulnerabilities, the only reason the score should change is either because new vulnerabilities emerge, new exploits are developed for old vulnerabilities or the site itself is changed.
- Comparability – The scores should allow one organisation to be compared with another even those of different sizes in different sectors.
- Resilient – The scores should also be comparable over time, the risk represented by a score this year should be broadly the same as the risk represented by a score the next year.
- Transparency – Methodology behind the creation of scores should be open to scrutiny, the scores themselves should be easily understood and the relationship between the score and specific vulnerabilities should be clear to all. Edit visually